
This post is the fifth part of a series looking at cyber security supply chain risk management (C-SCRM).
In the previous post in this series we discussed the establishment of a C-SCRM policy for your business, and initial programme management tasks.
Today we are going to look at the tasks involved in assessing your current supply chain for cyber security.
What would this assessment involve?
While programmes will vary slightly, depending on how far your in-house team has progressed, the likely initial tasks will be to:
- Map the supply chain if this task was not conducted as part of programme setup earlier
- Prioritise supplied product or service types and identify relevant controls or requirements by type
- Determine the starting point: usually the highest-priority suppliers
- Develop a questionnaire for the suppliers to complete, to ensure consistency
- Determine whether you need additional tools and processes to support you in conducting and recording your findings
- Create a risk profile per supplier: often based on the data they use, or the criticality of their service to the business
- Conduct a gap analysis for existing supplier/supplied product or service against the security requirements for that product or service type
- Identify relevant controls or requirements for that product or service type
- Consider whether you will rely on your supplier’s certification, or whether you’ll want to check for yourself; this may vary depending on the risk profile of each supplier
- If appropriate and possible (given contractual limitations) work with suppliers on security gap improvements
- Prepare for contract renewal for each supplier (if appropriate) to fill any relevant contractual gaps.
Later tasks in the programme could include:
- Re-assess each supplier regularly based on risk profile
- Adjust risk profile as necessary
- Review the relevant security controls
- Continue to work with suppliers on security gap improvements
- Extend the process to lower priority suppliers.
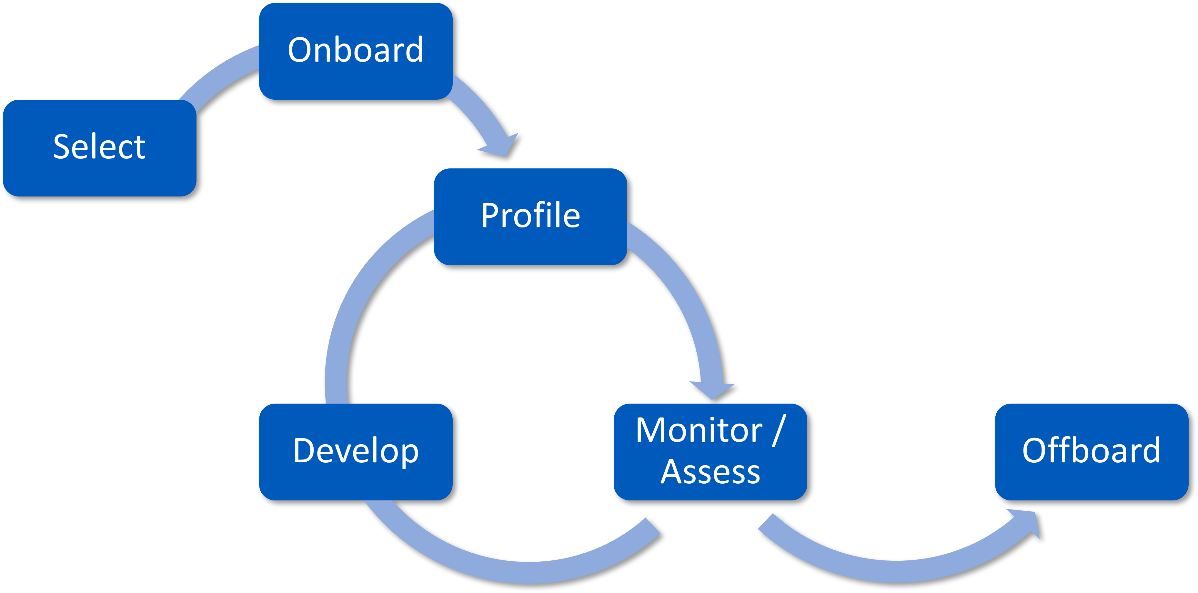
Figure 2: Supplier risk management lifecycle
Considering outsourcing?
Sometimes your supplier may prefer an independent view of their processes, rather than having their customer—you—delving into their (possibly sensitive) information and ways of working.
If you are considering outsourcing some or all of your C-SCRM programme to an external consultant, there are several questions you should consider:
- Which of these could you do yourself? How much have you already done?
- What skills will your consultant need to have?
- How much input will your partner need to support them in these tasks?
- How will you identify ‘high risk’ suppliers for your business – and what counts as ‘low’? Your partner will be able to help you with this, but it would be worth considering in advance. For example, which of your suppliers are essential to your process, such that if they were unavailable, your core operations would have to stop?
- What about suppliers to your suppliers – your fourth parties? Understanding the supply chain of your suppliers might reveal potential problems where multiple companies are relying on the same provider (known as concentration risk). While this isn’t necessarily related to cyber security risk, it could be a risk you should consider.
- C-SCRM work is likely to correlate with business continuity supplier analysis work – is someone already working on that, in your organisation? Can you share information between teams?
Potential challenges
C-SCRM isn’t easy and will take a while to put in place. There are number of potential challenges you may face:
- You are already in a contractual relationship with your existing suppliers, and they may be unwilling (or unable) to make changes mid-contract – or it might prove expensive for you to request the changes
- Some of your suppliers may be nearing their contract end / renewal date before you are ready with a changed renewal process; you will need to take this into account when creating a project plan.
- You may not have any leverage over some suppliers, perhaps because they are too big, or because you have no contract with them – consider open-source software, as an example. Suitable controls will need to be identified (such as using vetted and approved open-source libraries only).
Remember, it is all about risk management. How you choose to overcome these challenges is up to you.
What’s next?
In our next post, we will discuss the task of reviewing your current C-SCRM processes. This could be done in parallel with assessing the cyber security measures of your current suppliers if you have enough time and resources available. Of course, if you’d like help with any of these C-SCRM tasks, do contact us to discuss your requirements.
About CSP
CSP are a specialist security consultancy helping our clients navigate this increasingly interconnected world. Our team can:
- advise on security requirements, based on your situation
- assess your suppliers against your security requirements at every stage:
- reviewing their responses to security questions
- reviewing security clauses in contracts
- auditing your selected suppliers for compliance with your security requirements.
- work with you to enhance your policies and processes to improve security throughout your procurement process.









