
This post is the second part of a series of posts looking at cyber security supply chain risk management (C-SCRM).
When buying products or services, or when partnering with another organisation, you get access to something that your business needs.
This might be the materials, or a ready-made part needed to manufacture your product. It might be specialist skills and expertise that your organisation lacks. It could be support-tools to enable you to work (such as IT), or it could be supporting services that you prefer not to do yourself, because it is more cost-efficient to concentrate on what you do well.
Whatever it is you are acquiring, it is important to understand what the security risks are, and the security requirements placed on each party. Failure to communicate clearly is likely to lead to problems further down the road.
You might have specific security requirements for that product or service, either for your own purposes, or because a client of yours requires them from you. If you don’t explain those cyber security requirements for this product or service up front, your supplier won’t know what you need. This will make it hard for them to meet your (unspoken) expectations, and the relationship might not go as well as you’d hoped.
Your legal team will be able to detail the legal wording for different situations, but it is essential that you consider your security requirements in each case and discuss them in advance. Drafting—in advance—security requirements that could be used in different circumstances would be useful.
As well as clauses intended to protect company confidential information, there are very likely to be specific requirements for the protection of sensitive, IP or financial information or personally identifiable information, in line with the Data Protection Act responsibilities. And there may well be additional security-related requirements, depending on the nature of the product or service to be supplied.
Security requirements and contracts
There are several security-related requirements to consider including in contractual arrangements with your supplier, such as:
- Any security requirements relevant to the specific product or service being supplied. This will vary widely by supplier—supply of a training day hosted offsite will not have the same security requirements as the provision of IT infrastructure. These requirements must be identified (as far as is possible) before going out to market.
- Define security responsibilities – explaining everything that needs to be clearly understood and implemented.
- That they have in place plans and procedures to enable them to respond quickly and efficiently to a cyber security incident.
- That they notify you of any security issues or incident likely to affect either party’s cyber security.
- That they share with you any information they have or learn that might help you to mitigate any such cyber security incident.
- That they have in place a business continuity plan to enable them to be able to continue to provide services to you.
- That all security-related information supplied as part of the procurement process (for example in the supplier questionnaire) forms part of the contract. This is because the contract award may be dependent on the information provided during risk profiling and assessment of the supplier being accurate.
- That your supplier manages their own supply chain risk to the same (or other, agreed) level of security as you are managing yours.
- Information classification – what you see as ‘Confidential’ may mean something completely different and be treated very differently within your supplier’s environment.
- Right to audit / conduct regular assessment of their security practices, and to monitor and measure performance. You’ll need to be able to check that everything is going to plan, including the management of any security gaps.
- Communication of details of any situations where adherence to the security requirements is not possible, so that the resulting security gap can be managed. Understanding these gaps, and working to manage them, will be an important part of managing your supply chain security once the supplier has been onboarded.
- Provision of appropriate treatment for known vulnerabilities that could impact you.
- Provision of independent evidence (for instance, by third party audit) that they are complying with contractual requirements. This won’t be relevant for every supplier and will depend on the risk presented by the contract.
- Timely communication of any other changes in their organisation that may affect your business. Nobody likes to discover with no notice that, for example, a vital and knowledgeable resource is being reallocated and won’t be available to support you.
It is, of course, important to recognize that you are part of an ongoing supply chain and should be prepared to support your customers in the same way. Your customers will, if not already, be asking these questions of you, so it is worth having the answers prepared.
Categorising your suppliers
Not all the clauses outlined above will be relevant to all suppliers. The contractual agreements should be relevant to the supplied product or service and proportionate to the risk that each supplier presents. For example, asking low-risk suppliers to provide independent evidence via third-party audit that they are complying with your requirements would be overly stringent and impact relationships negatively.
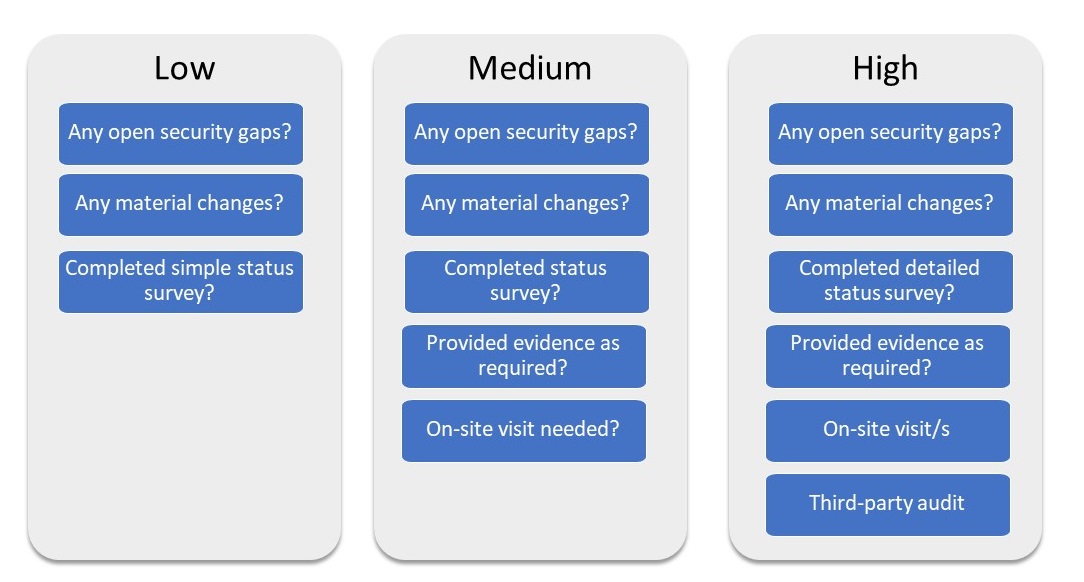
Example: Use different levels of due diligence depending on your assessment
Don’t forget to include your cloud or SaaS services for consideration. These are just as important as on-premise—perhaps even more so.
Consider developing a risk profile for each supplier as part of the supplier assessment process, based on a range of things including:
- What they are supplying and how important it is to your business.
- Whether data is being shared and handled electronically.
- Whether the supplier has access to your systems.
- Whether they are supplying a product or service to support information processing and/or that could make your data available via the internet.
- And where the supplier is based.
Once you have a risk profile for a supplier, you can manage them based on this profile at every stage of procurement. Low risk suppliers should have different questionnaires to complete, less strenuous assessments post-contract, and a different set of contractual clauses to the higher-risk suppliers.
Do tell your suppliers you are developing your C-SCRM programme; be transparent and reassure them that you are not interested in their sensitive data but are working for the benefit of both.
Conclusion
In general, though, by summarising these clauses, we can see that at some level they are applicable to all, requiring:
- Clear and regular communication of any security gaps or incidents, significant changes and pooling any useful information to reduce risk to either party.
- Identification and inclusion of security requirements, both in general and specifically for the product or service being supplied.
- Good security practices, governance, and management at your supplier—and at their suppliers.
- Audit, monitoring and measuring rights.
Of course, if you must rely on your contractual clauses to ensure that what you expect to receive is delivered, the relationship is already broken. But at least by clearly communicating in the contract what you expect, your supplier will know exactly what you want from the beginning—and so will you.
In future posts, we will talk about:
- Planning for success when outsourcing C-SCRM
- Developing a C-SCRM policy and programme
- Assessing current suppliers: where are the security gaps?
- Reviewing current processes: what could we do better?
- Implementing and embedding a C-SCRM programme
About CSP
CSP are a specialist security consultancy helping our clients navigate this increasingly interconnected world. Our team can:
- advise on security requirements, based on your situation
- assess your suppliers against your security requirements at every stage:
- reviewing their responses to security questions
- reviewing security clauses in contracts
- auditing your selected suppliers for compliance with your security requirements.
- work with you to enhance your policies and processes to improve security throughout your procurement process.
Please contact us here or call us on 0113 5323763 to talk about how we can help.








