This post is the third part of a series looking at cyber security supply chain risk management (C-SCRM).
If you are thinking of outsourcing some or all of your C-SCRM programme to an independent or external consultant, there are some things to consider, both beforehand and during the process, to avoid issues arising later.
Preparation and planning
Before going to market to find someone to take on the C-SCRM programme for you (or, indeed, any work on your behalf), you should:
- Understand what you want to achieve
- Understand what you can or can’t do yourself
- Clearly specify what you need your partner to do.
By providing clarity at the beginning about exactly what you want from your consultant – and being transparent about what your in-house team will be able to do (and when) – you’ll get the best result. They’ll have a better understanding of your needs, and you’ll be able to track progress towards your goals.
Consider what your desired outcome will be, and then what you will need to put in place to achieve this result. This series of posts is focused on the processes needed, so you can complete the programme in-house, or outsource it if that is what you prefer.
If your decision is to outsource, it is important to find the right partner. Obviously, they should have the skills to do what you need, but you’ll also need to be able to work with them, and to trust them with the details of your business.
However, while trust is important, you should also agree with them the timescales for the work, any milestones, the budget, and a reporting pattern, so that you can track progress. Putting governance in place and ensuring two-way communication throughout will be essential for success.
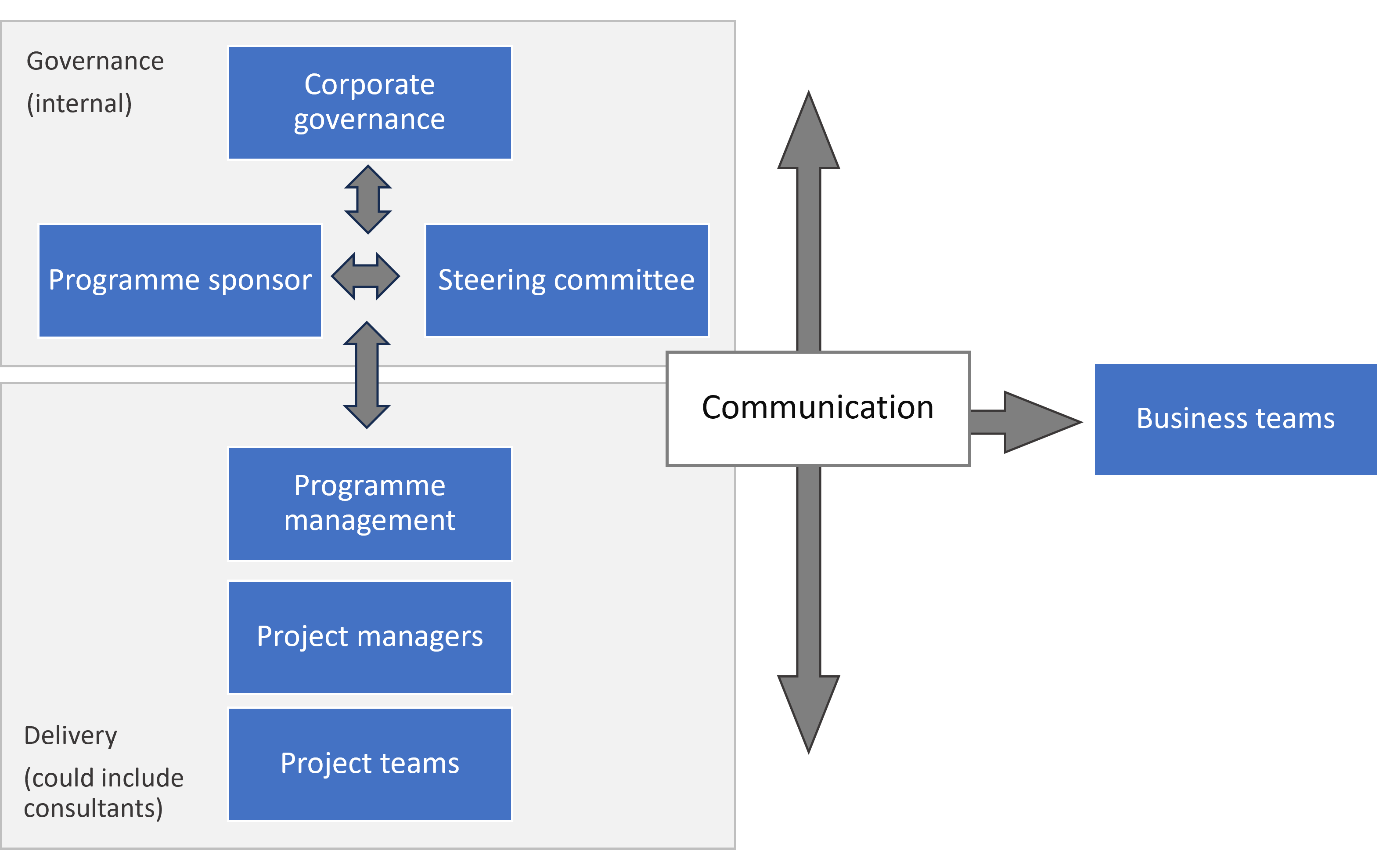
Communication is key
The most common problems arising from outsourcing part of your business activities come from lack of clear communication.
To be able to support your business with C-SCRM, your consultant will need information from you – about the business and your plans, about your policies and processes, about the cyber security controls you already have in place, about your suppliers, and about your position on risk. They also need to understand exactly what you want from them, and which elements you will do in-house.
Depending on what you’ve tasked your consultants to produce, they may need to work with a wide range of people in your organisation, such as information security, procurement, IT, software development, legal and HR. The importance of this programme to the business should be communicated to these departments or individuals.
Similarly, to ensure that you get the best result from your consultant, you will need information from them. They should report progress regularly, raising any issues that affect progress on the work you have tasked them with. If they raise anything else that might be an issue for your business, you should take note: while it might not be part of this project, and therefore out of their agreed scope, it may be something you should consider acting on. And of course, if there is anything in their advice that is unclear, you should ask them to explain.
Elements of C-SCRM to consider for outsourcing
In the next few blog posts, we will look at some of the elements of C-SCRM that you could consider outsourcing to an external consultant:
- Developing your C-SCRM policy and setting up a C-SCRM programme
- Assessing cyber security in your current supply chain
- Reviewing your current C-SCRM processes
- Implementing a C-SCRM programme
If you do decide to outsource some of these tasks, we’d be happy to talk about how we can help. Contact us on 0113 5323763 to find out more.
About CSP
CSP are a specialist security consultancy helping our clients navigate this increasingly interconnected world. Our team can:
- advise on security requirements, based on your situation
- assess your suppliers against your security requirements at every stage:
- reviewing their responses to security questions
- reviewing security clauses in contracts
- auditing your selected suppliers for compliance with your security requirements.
- work with you to enhance your policies and processes to improve security throughout your procurement process.