
This post is the sixth part of a series looking at cyber security supply chain risk management (C-SCRM).
In the last post, we looked at one of the early projects in a cyber security supplier assessment risk management programme: assessing your existing suppliers. In this post, we will consider supplier management process review. This is to ensure that your processes are appropriate throughout the contract period, and that you retain control of your risk profile.
These processes cover onboarding of your suppliers, and then the management of those suppliers throughout their engagement with your business:
- Procurement and onboarding
- Supplier lifecycle management
The aim will be to ensure that security is considered at every stage of each process – but only if relevant. If you are buying paperclips and printer paper, for instance, the cyber security risk will be low (but not non-existent, if you are buying online) and won’t need extensive assessment. However, if this is a trusted supplier with email access and perhaps IT access, then the risk will be significantly higher. For example, they (or someone pretending to be them) could forward malware via email and—because they are trusted—your staff are more likely to accept the email at face value and click the malicious link or download the attached malware.
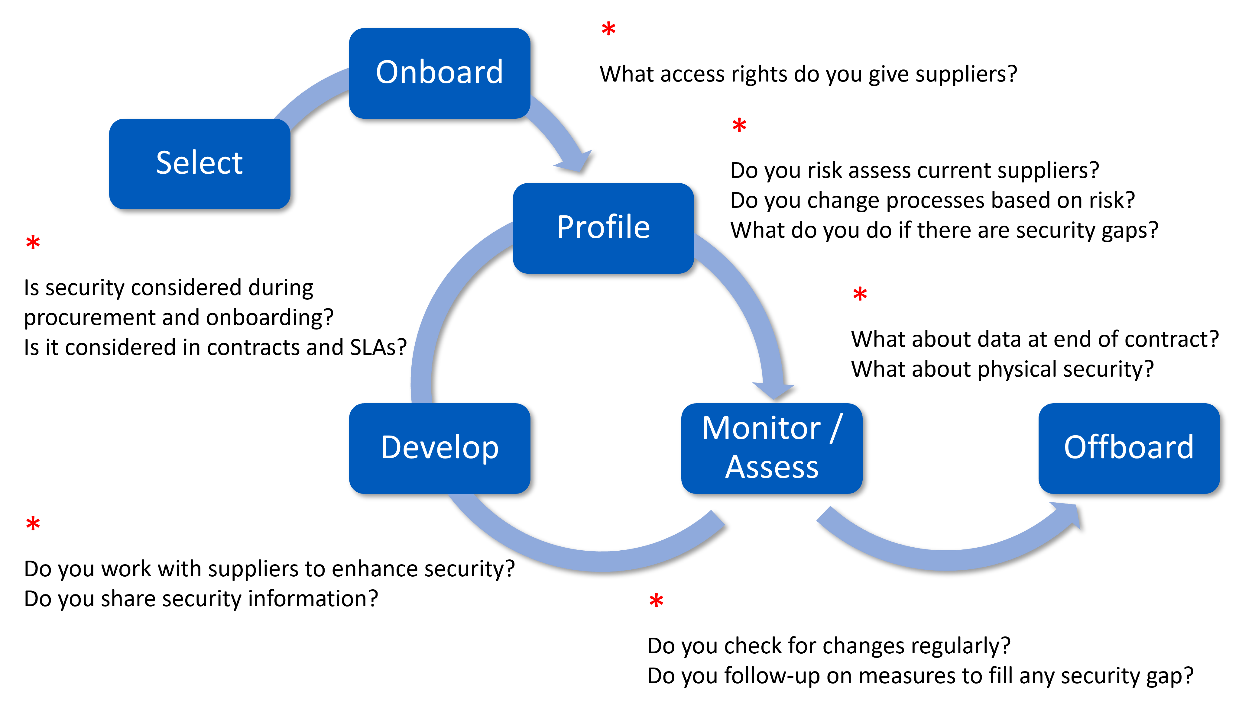
Figure 2: Supplier risk management lifecycle
Procurement and Onboarding
A critical part of the C-SCRM programme will be to review your current procurement and onboarding processes, to ensure that cyber security is considered as part of selection, in the contract agreements, and when onboarding a new supplier.
Questions to think about include:
- Does your procurement process include cyber security as a gauge of suitability? For instance, does your initial risk assessment - often conducted via a questionnaire - ask about (if relevant): secure development lifecycle? Penetration testing? Certifications?
- If you will be sharing data with the supplier, do you ask where the data will be stored? How it will be transferred?
- What about business continuity: do you discuss availability of service, and what their continuity plans are?
- What about the contracts – will they include, for example, the right to conduct security audits, security related SLAs, flowdowns of control requirements to subcontractors if applicable, and milestones for remediation of any security gaps?
Supplier Lifecycle Management (Ongoing and Offboarding)
Reviewing the current processes for supplier management once they are providing their product or service to you will indicate whether the cyber security of your suppliers is considered now. Don’t forget to think about how cyber security is handled at the end of the contract too.
Questions to think about include:
- What processes do you have in place already to risk-assess current suppliers?
- Are these differentiated by assessed risk?
- How will you be alerted if there is a cyber security incident (or indeed, any other incident that might impact your business continuity) at your supplier?
- Will you consider a lighter touch for the second and subsequent years of the contract? Ongoing checks on security may be just as important as the initial check.
- How do you ensure the security at contract-end of any data that your supplier has been processing on your behalf? What about physical access to any of your buildings?
Once the review is complete, it should be clear where there are gaps in the cyber security aspect of your supply chain risk management processes.
The next step will be to establish whether any of those gaps can be closed, and if so, how. Implementing new controls and processes will be the next step.
Outsourcing Considerations
There’s a lot to think about in this phase of the programme; outsourcing these tasks can reduce your own workload and ensure that the phase is completed on time.
Be aware, though, that whoever does this work on your behalf will still need input from you and your staff to understand how these processes work in your business.
About CSP
CSP are a specialist security consultancy helping our clients navigate this increasingly interconnected world. Our team can:
- advise on security requirements, based on your situation
- assess your suppliers against your security requirements at every stage:
- reviewing their responses to security questions
- reviewing security clauses in contracts
- auditing your selected suppliers for compliance with your security requirements.
- work with you to enhance your policies and processes to improve security throughout your procurement process.









