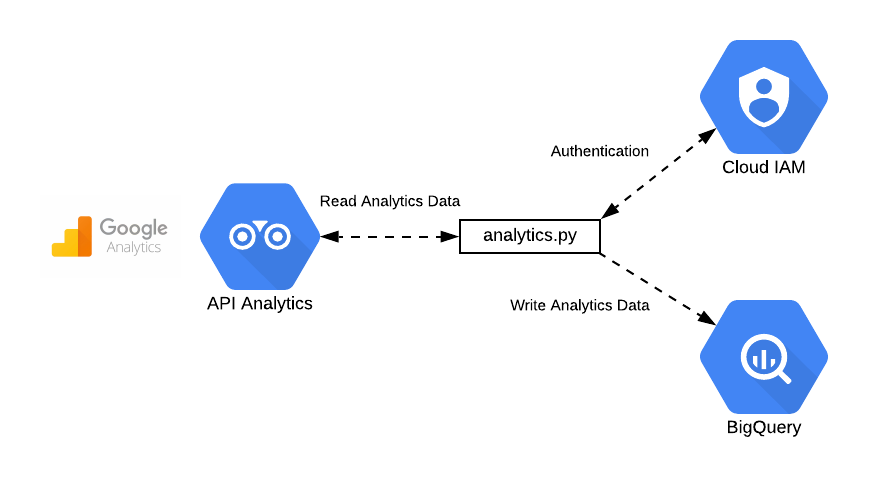
In companies of all sizes, it isn’t uncommon to find that core cloud resources and applications that are used every day are not actually managed by, or integrated into the overall IT infrastructure. This unstructured and unmanaged environment is what we call ‘shadow cloud’.
On a well-organised network that leverages a foundation such as Enterprise DNS (a suite of DNS, DHCP, and IPAM solutions), devices are covered by a unified, secure system. On a ‘rogue cloud’, nobody knows for sure what is going on. Although AWS, Google and Azure come secure and robust firewalls, utilising them correctly slows down testing processes. Naturally, these firewalls also get indiscriminately disabled by the same users that circumvented the corporate IT processes in the first place.
How often is it happening?
A Symantec report “Avoiding The Hidden Costs of the Cloud” collected data from 3,236 organisations across 29 countries - both SMBs and enterprises. The report found that rogue cloud computing use was reported in 83% of enterprises and 70% of SMBs.
However, shadow cloud users aren’t mavericks or fools. They are simply trying to do their job as best they can against a backdrop of contradictory constraints set by their corporate leaders, often simply attempting to get things done fast whilst waiting patiently to be granted the resources they need. Rogue cloud mainly stems from a mix of clashing team priorities and modernisation-inhibiting network architectures.
The most common reason for these rogue cloud projects is the perception that they will save time and money. Employees feel that getting permission from IT or management would make the process far trickier and slower.
Another common scenario for their existence is when the company’s IT services are unable to provide solutions in a suitable timeframe. Complex processes and requirements can slow the delivery time which eventually becomes unsuitable for the project. Development teams, especially at the world’s largest organisations, move at a lightning pace. Not just to keep their businesses competitive, but also to keep their jobs.
What are the consequences?
Ultimately, businesses are unable to provide or allow cloud resources that are available on the open market and their employees who want to use these resources in their projects are frequently cited. The potential consequences of these shadow clouds include:
- Escalation in cost
- Increasing complexity in backing up and storing data, and inefficient storage services
- Risk of confidential information exposure
- Account takeover security risk
- Misappropriated use of goods or services as processing power, storage and network services
- Problems in budgeting for proper corporate process to be established, to meet the actual long-term demand
Is anyone to blame?
So where does responsibility lie for this problem? In one out of every six cases of shadow and rogue cloud, the empowered employees simply do not realise that they should not create these shadow environments.
As highlighted, most of these employees have acted with the best of intentions. The reason employees engage in rogue clouds in the first place is to save time and avoid cumbersome processes; therefore, figuring out how to balance employees’ time with the security needs of your company is imperative.
How do you detect rogue clouds?
Ultimately, we can use network traffic analysis to discover any rogue cloud. However, whilst a properly configured next-generation firewall and appropriate software can do this, the work required to do so is significant.
An effective way to identify the existence of any shadow cloud is to examine the credit card statements when employees submit expenses and identify them via the costs incurred. Higher-end expense tracking solutions can actually be configured to flag specific expense types, so finding them can be at least somewhat automated. However, the next step is critical - reaching out to the employees in a positive way, rather than coming down hard on them.
The solution - embrace shadow cloud?
It is essential to remember, however, that every rogue service identified (whether it is on AWS, Google or Azure, or something more self-contained such as Salesforce), is a symptom of an unmet need. The employees need services, and either the organisation could not provide the service when they needed it, or they were not aware they could access it. Either way, the root cause of the shadow cloud problem lies with IT.
The dilemma for management is if they try to prevent this sort of activity with the proverbial iron fist, the activity will be likely to continue more discretely behind the scenes - and they ultimately run the very real risk of having a security incident or a business failure that could potentially require far more resources than ever imagined!
Potential solutions to avoid reaching this conclusion include the following:
- Investing in training around the shadow cloud risks and how they can affect the company business
- Creating mechanisms to improve deployment times, enabling self-service portals and preconfigured environments for employees
- Addressing the existing slow service level agreement / IT issues
- Adopting a federated approach through a secure directory service, that allows integrating distinct cloud providers under the company supervision and policies
The research from Symantec highlighted the high prevalence of rogue cloud computing amongst the majority of both large and small organisations, and this situation is unlikely to change any time soon. Given the cost implications and the potential risks to the business, IT management need to really focus on creating a workable solution and ideally solve the underlying issues and frustration that drives the creation of rogue cloud usage.
In so doing, they should ensure they bring the energy and willingness of the workforce with them, to create a set of corporate IT services that meets the needs of the team, and the future IT aspirations of the organisation.